9. Jun 2021
Warning of phishing – Please check sender and domain name
Currently, phishing e-mails are being sent that contain original e-mails from correspondence with university members as attachments and can therefore appear deceptively real.
Check sender
Please make sure that the sender is plausible. Most university members use their university e-mail address in the form firstname.lastname@institution.uni-halle.de for sending. Some e-mail programs show the sender’s address only after double-clicking on the sender’s name.
How to deal with links
If possible, please do not open any links from e-mails: If, for example, a document of a Stud.IP event is linked, you can open Stud.IP directly via the URL you know https://studip.uni-halle.de/ and locate the document by going to the file area of the event. If this is not an option, check whether the domain name of the link ends with „uni-halle.de“ and is therefore trustworthy.
The displayed text of a link and the target address (URL) are not necessarily identical. An example in which the text is https://uni-halle.de/, but the target address is https://uni-halle.org/: https://uni-halle.de/
To do this, right-click the link (usually a long tap on touch devices) and copy the target address (URL) to the clipboard. Then paste the content of the clipboard into the browser’s address bar and scroll to the top. Now, determine if you trust the page by examining the domain of the URL.
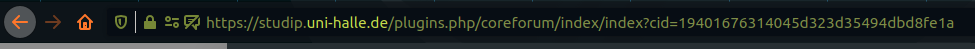
In this example, the domain is „studip.uni-halle.de“ . The component „uni-halle.de“ has already been highlighted by the browser. Trusting this domain, you can now open the page by clicking on „Enter“, „⏎“, „➞“ or „Go“, depending on your operating system.
Case study
With this in mind, now consider the following screenshot:
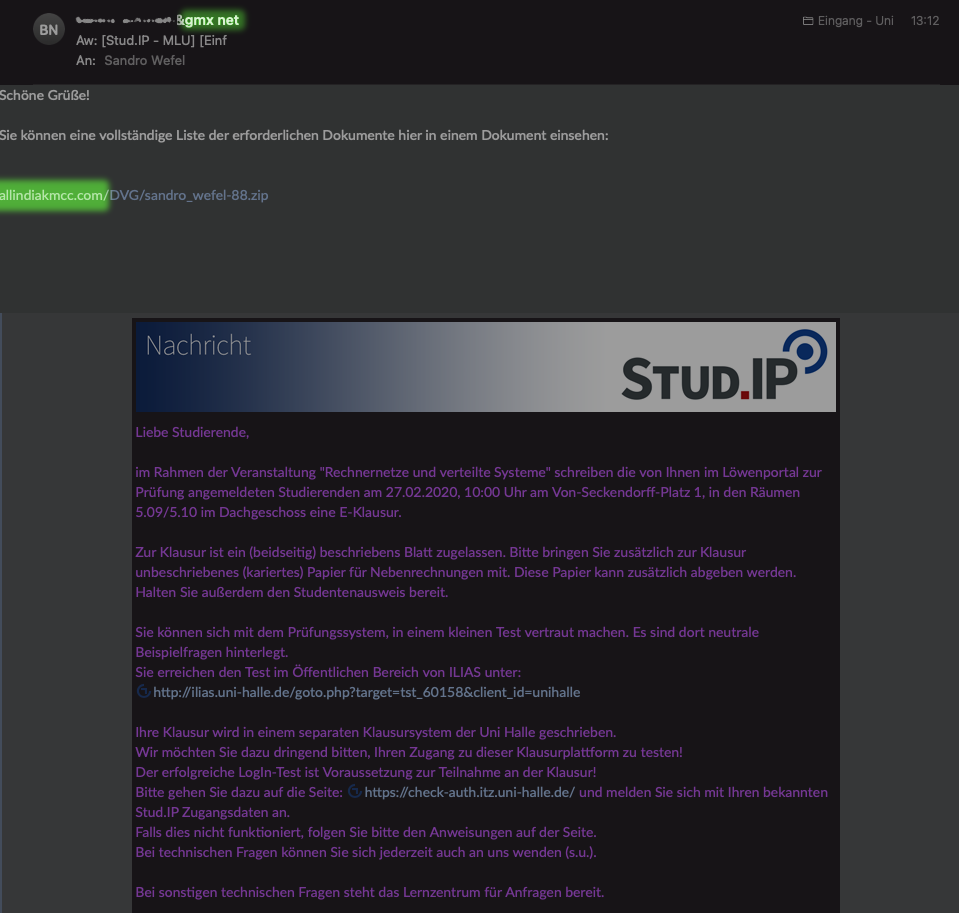
Already highlighted are the components by which you can recognize at first glance that this is probably phishing:
- Possibly sent from a GMX address. Most lecturers would probably use their official firstname.lastname@institution.uni-halle.de e-mail address.
- A ZIP file is offered via the domain name „allindiakmcc dot com“. Most lecturers would probably upload material on Stud.IP ( https://studip.uni-halle.de/ ) or ILIAS ( https://ilias.uni-halle.de/ ).
In addition, you may be skeptical about the salutation „Greetings“ or the provision of additional documents that are not required or necessary.
Further information
For more information on e-mails with questionable content, check out the ITZ-Blog.
What to do if I entered my password on a fake website?
You can set a new password on https://serviceportal.itz.uni-halle.de/. If this is no longer possible, please contact the ITZ Helpdesk immediately: +49 (0) 345 55 21 888 helpdesk@itz.uni-halle.de